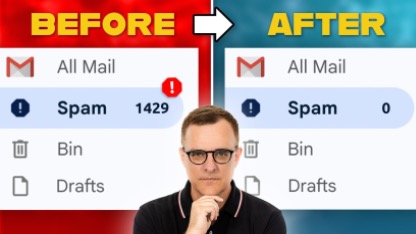
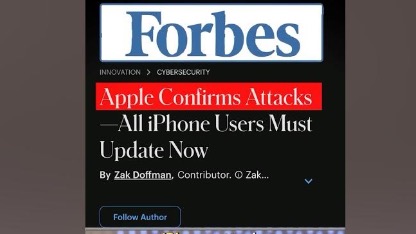
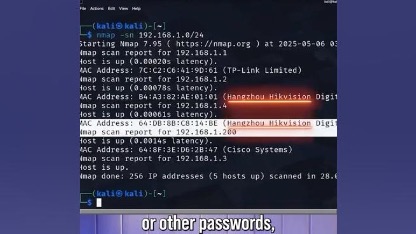
Update Now!
Apple Confirms Attacks—All iPhone Users Must Update Now: Sources: Forbes: https://www.forbes.com/sites/zakdoffman/2025/12/13/ios-262-apple-confirms-iphone-attacks-you-must-update-now/ Bleepingcomputer: https://www.bleepingcomputer.com/news/security/apple-fixes-two-zero-day-flaws-exploited-in-sophisticated-attacks/ #apple #iphone #cybersecurity